XM Vulnerability Exploit Attempts

Index
Overview
This post is an analysis of hacker reconnaissance and exploit attempts related to the 2023 critical security bulletins. Insights can be extracted for existing and future XM/XP implementations.
I have been sitting on this data for 2 years. Now that the dust has settled and everyone has had plenty of time to patch their environments, I'm finally able to share it with you. Due to the amount of analysis and writing that this post required, I used Cursor to help me write it (with a lot of babysitting).
This comprehensive analysis will walk you through:
- Infrastructure Details: Which environments were targeted and which were not
- Vulnerability Specifics: Technical breakdowns of CVE-2023-33651 and CVE-2023-35815
- Attack Patterns: Real-world exploit attempts captured in IIS logs
- IP Intelligence: Detailed information about the attacking IPs, their locations, and ISPs
- Temporal Analysis: When attacks occurred and how they evolved over time
- Defensive Insights: What you can learn to better protect your own implementations
The data presented here is from an actual production system, providing a unique window into how attackers operate in the wild.
The following table illustrates the infrastructure that was in place at the time (now decommissioned):
| Server | Targeted by Attackers |
|---|---|
| STAGING CM | Yes |
| STAGING CD | No |
| PROD CM | Yes |
| PROD CD1 | No |
| PROD CD2 | Yes |
To the best of my knowledge, patches and mitigations were in place prior to the attack patterns being observed in the logs.
The Vulnerabilities
The 2023/2024 security bulletins addressed several critical vulnerabilities in Sitecore XM/XP. Understanding these vulnerabilities is essential for appreciating the attack patterns observed in the logs. This section provides technical details on the two primary vulnerabilities that were actively exploited by threat actors.
The relevant security bulletins are:
- SC2023-001-568150: Related to the MVC Device Simulator vulnerability which might allow IIS Authorization Rules Bypass.
- SC2023-002-576660: Related to remote code execution vulnerability.
- SC2023-003-587441 (supersedes the prior two): Addresses Critical (582720) and High (584731) severity vulnerabilities in Sitecore software. Successful exploitation of the related vulnerabilities might lead to remote code execution vulnerability and non-authorized access to information.
- SC2024-002-624693: Related to remote code execution through insecure deserialization (CVE-2025-27218).
DeviceSimulator Path Traversal & Unauthorized Access
Security Bulletin: SC2023-001-568150
Announcement Date: March 28, 2023
Superseded By: SC2023-003-587441 (June 20, 2023)
CVE: CVE-2023-33651
Severity: Critical
References:
- KB1002925
- KB1003018 (superseding bulletin)
- Assetnote Research
Technical Overview
The DeviceSimulator vulnerability exploits the Mobile Device Simulator feature in Sitecore, which allows content authors to preview how their site appears on different devices. The vulnerability exists in the Sitecore.Mvc.DeviceSimulator.Controllers.SimulatorController component and can be exploited through path manipulation.
The vulnerable endpoint is typically accessed at:
Attack Vectors
1. Path Traversal for File Read
Attackers can use the previewPath parameter to read arbitrary files from the webroot by bypassing IIS authorization checks. The most commonly targeted file is the license file, which can reveal sensitive information about the Sitecore installation:
The vulnerability allows reading files that would normally be protected by IIS authorization rules, because the preview functionality processes the path in a way that circumvents these protections.
2. Chaining with Execute.aspx
More sophisticated attacks observed in the logs attempted to chain this vulnerability with access to Execute.aspx, a powerful Sitecore administrative interface:
If successful, this chain could enable arbitrary code execution, as Execute.aspx provides direct access to Sitecore's backend operations.
Why This Works
The vulnerability relies on a combination of factors:
- IIS Authorization Bypass: The request is processed through the MVC pipeline in a way that bypasses standard IIS authentication and authorization checks
- Path Manipulation: The
previewPathparameter is not properly sanitized, allowing traversal to protected resources - Privileged Context: The preview functionality runs in a context that has access to restricted paths
Affected Versions
- Sitecore Experience Platform 9.0 rev. 171002 (Initial Release) +
- Content Delivery, Content Management, Reporting, Processing, EXM Dispatch
Timeline Context
Exploitation in the wild began remarkably quickly after the details of the vulnerabilities were made public:
- March 28, 2023: Sitecore publishes SC2023-001-568150
- May 10, 2023: Assetnote publishes technical exploitation details
- May 12, 2023: First observed exploit attempts (2 days after technical disclosure)
This rapid weaponization highlights the importance of applying security patches before technical details become public.
sitecore_xaml Deserialization & Remote Code Execution
Security Bulletin: Not explicitly numbered in logs, but related to XAML deserialization vulnerabilities
Known Since: Pre-2023 (various iterations)
CVE: Related to CVE-2021-42237 and similar deserialization issues
Severity: Critical
References:
Technical Overview
The sitecore_xaml.ashx vulnerability is a deserialization attack that exploits Sitecore's XAML handling capabilities. XAML (eXtensible Application Markup Language) is a declarative XML-based language used in .NET applications, and when user-controlled XAML is deserialized without proper validation, it can lead to remote code execution.
The vulnerable endpoint is:
Attack Mechanism
1. XAML Injection with TemplateParser
The attack exploits ASP.NET's TemplateParser.ParseControl method through XAML deserialization. By crafting malicious XAML that invokes this method, attackers can execute arbitrary code:
2. The Deserialization Chain
The exploitation chain works as follows:
- Attacker sends malicious XAML to
sitecore_xaml.ashx - Sitecore processes the XAML without adequate validation
- The XAML invokes
TemplateParser.ParseControlvia reflection - This allows instantiation of arbitrary .NET types
- The attacker chains gadgets to achieve code execution
3. Copy-Paste Exploitation
A significant observation from the December 31, 2023 logs is that attackers used the exact payload from the Code White research blog, including the same marker string Z03Oq1. This indicates script-kiddie-level exploitation where attackers copy published proof-of-concept code without modification.
The exception logged on staging reveals the attack was caught by Sitecore's reflection protections:
This suggests that while the infrastructure had protections in place, the vulnerability was still being actively probed.
Why This Is Dangerous
- Remote Code Execution: Successful exploitation grants arbitrary code execution on the web server
- No Authentication Required: The endpoint can be accessed without authentication on vulnerable systems
- Widespread Targeting: The logs show consistent, global exploitation attempts across multiple IP ranges
Timeline
The high level timeline is as follows:
Specifics:
-
March 28, 2023: Sitecore Security Bulletin SC2023-001-568150 (DeviceSimulator)
KB1002925 is posted. -
May 10, 2023: Exploit Details Published
Assetnote research published technical details: bypass IIS authorization … DeviceSimulator
Threat actor reconnaissance began just two days after publication. -
May 12, 2023: STAGING: First DeviceSimulator Requests
A GET request to.../SimulatorController,Sitecore.Mvc.DeviceSimulator.dll/PreviewwithpreviewPath=/App_Data/license.xml(returned a 404) indicates early reconnaissance for the DeviceSimulator vector. -
May 15, 2023: STAGING: Additional DeviceSimulator Requests
Repeated requests topreviewPath=/App_Data/license.xmlwith varied user-agents (all returned 404). -
May 17, 2023: STAGING: Expanded DeviceSimulator Variants
previewPathvariations including/App_Data/license.xmland/Data/license.xml, including escaped forms (all returned 404). -
June 20, 2023: Sitecore Security Bulletin SC2023-003-587441
KB1003018 posted.
This bulletin superseded the March bulletin KB1002925 (SC2023-001-568150), as in, if the permanent solution from this bulletin was applied, the solution specified in the previous bulletin was no longer necessary. -
July 7, 2023: PROD CD2: SimulatorController Targeting Execute.aspx
Multiple GET/POST requests to.../SimulatorController,Sitecore.Mvc.DeviceSimulator.dll/PreviewusingpreviewPath=/sitecore/shell/Applications/Content Manager/Execute.aspx?cmd=...(returned 404/301).
Interpretation: Targeting DeviceSimulator preview path to reachExecute.aspxcommand surface. -
October 11, 2023: STAGING: sitecore_xaml Activity With site=site2
Series of calls tositecore_xaml.ashx/...with follow-up to/sitecore/service/notfound.aspx?item=/sitecore_xaml&...&site=site2.
These entries are particularly interesting because of the inclusion ofsite2in thesiteparam. This indicates manual work by the hacker or more fine tuned automation of pen testing. -
October 11, 2023: PROD CM: Earliest sitecore_xaml Attempts
POST tositecore_xaml.ashx/-/xaml/Sitecore.Xaml.Tutorials.Styles.Index(403). -
October 17, 2023: Continued sitecore_xaml Attempts
Additional POST attempts on STAGING endpoint: -
October 22, 2023: PROD CM: sitecore_xaml Attempt
POST attempt (403). -
November 2, 2023: PROD CM: sitecore_xaml Attempt
POST attempt (403). -
December 4, 2023: PROD CM: sitecore_xaml Attempt
POST attempt (403). -
December 14, 2023: STAGING CM and PROD CM: Initial Probes
Requests to/(301) and/default.js(200) usingcurlandpython-requests. -
December 18, 2023: STAGING CM and PROD CM: Follow-up Probes
Repeat of/(301) and/default.js(200) probe pattern. -
December 31, 2023: STAGING CM: Notable Exception Captured
ExceptionAccessDeniedExceptiontriggered bysitecore_xaml.ashxpayload (see analysis in Code White). This one is interesting because the arbitrary string that was injected is the exact same one as the post that demonstrated the exploit. The hacker simply copy and pasted it. This request was performed only on STAGING CM and not on any of the other sites / environments.The IP address
86.106.158.99is based out of Switzerland, so I already know that this is probably a hacker, given that the site I was performing this analysis on was unlikely to have legitimate visitors from Switzerland. A HTTP request to the IP returns a Ubuntu splash page. It is still up and running as of November 2025. -
December 31, 2023: STAGING CM: IIS POST to sitecore_xaml
POST tositecore_xaml.ashx/-/xaml/Sitecore.Xaml.Tutorials.Styles.Index(302). -
December 31, 2023: PROD CM: sitecore_xaml POST Attempt
POST attempt tositecore_xaml.ashx/...(403). -
January, 2024: Probing Continues
General probing shows up in the logs again on January 9, 10, 11, 12. -
January 16, 2024: PROD CM: Additional sitecore_xaml Attempts
Multiple POST attempts (403). -
January 18, 2024: PROD CM: Additional sitecore_xaml Attempt
POST attempt (403). -
January 20 and 21 2024
Probing continues. -
January 24, 2024: DeviceSimulator Preview Requests Return 401
Request to.../SimulatorController,Sitecore.Mvc.DeviceSimulator.dll/Preview?previewPath=/App_Data/license.xml(401). -
January 28, 2024: PROD CM: DeviceSimulator Preview Request 401
- Evidence:
previewPath=/App_Data/license.xml(401). - Reference: KB1002925
- Evidence:
-
January 28, 2024: Additional DeviceSimulator Preview Requests 401
Repeated 401 responses forpreviewPath=/App_Data/license.xml. -
January 29, 2024: Additional DeviceSimulator Preview Requests 401
Continued 401 responses forpreviewPath=/App_Data/license.xml. -
February 3, 2024: PROD CM: Additional sitecore_xaml Attempt
POST attempt (403). -
February 4, 2024: Additional Countermeasures Applied
IP address blocks added and IIS rules updated.
Attack Pattern Analysis
From the logs, we can observe:
- Frequency: Sustained attacks from October 2023 through February 2024
- Global Sources: IP addresses from multiple countries (Switzerland, China, Australia, Pakistan, various US locations)
- Automated Nature: Consistent user agent patterns suggesting automated scanning tools
- Response Codes:
403on PROD CM (properly protected)302on STAGING (redirecting, potentially vulnerable)404in some cases (handler not found or disabled)
Affected Versions
- Sitecore Experience Platform 8.x through 10.2 (specific versions vary by configuration)
- Systems with XAML preview functionality enabled
- Particularly dangerous on CM servers exposed to the internet
The Offending IPs
In this section, we will detail the activity of the offending IPs. Search your logs for these, as they are directly associated with reconnaissance/exploit attempts.
Note: The IP addresses listed below are current as of November 2025. IP allocations and hosting may change over time, so network ownership, location, or usage profiles could have been different at the time of the events documented above. Also, some of these IP addresses may be security researchers.
IPs that appear in log snippets within this post:
Other IPs that were associated with probing/attacks but do not appear in log snippets within this post:
20.86.112.4
This IP attempted to exploit hundreds of different vulnerabilities, and it did so slowly and with altered user agents. This IP is unique in that not only did it attempt to exploit all of the usual WordPress/PHP vulnerabilities, but it also attempted to exploit Sitecore-specific vulnerabilities. This indicates that Sitecore exploits are beginning to be included in common exploit kits, signalling a sign of maturity in the exploit kit industry and a sign that Sitecore is becoming more popular.
86.106.158.99
This IP address exhibited systematic reconnaissance and exploitation attempts across multiple dates and servers. The activity pattern suggests automated scanning with deliberate variation in user agents to evade detection.
Activity Timeline:
-
December 14, 2023: Initial reconnaissance on STAGE CM
- 21:29:35 UTC - GET request to
/ - 21:29:35 UTC - GET request to
/default.js - User agents:
curl/7.81.0andpython-requests/2.25.1 - Responses: 301 redirect for root, 200 success for default.js
- 21:29:35 UTC - GET request to
-
December 18, 2023: Repeated reconnaissance on STAGE CM
- 21:30:55 UTC - GET request to
/ - 21:30:55 UTC - GET request to
/default.js - User agents:
curl/7.81.0andpython-requests/2.25.1 - Responses: 301 redirect for root, 200 success for default.js
- 21:30:55 UTC - GET request to
-
December 31, 2023: XAML Tutorials vulnerability exploitation attempt on STAGE CM
- 13:14:02 UTC - HEAD request to
/ - 13:14:04 UTC - POST to
/sitecore_xaml.ashx/-/xaml/Sitecore.Xaml.Tutorials.Styles.Index - User agents: Varied Mozilla/5.0 Chrome user agents (Windows NT 6.1 and NT 5.1)
- Responses: 301 redirect for root, 302 redirect for XAML request
- 13:14:02 UTC - HEAD request to
-
January 21, 2024: Multiple DeviceSimulator exploit attempts on PROD CD2
- 13:03:52 UTC - Four consecutive GET requests to
/api/sitecore/Sitecore.Mvc.DeviceSimulator.Controllers.SimulatorController,Sitecore.Mvc.DeviceSimulator.dll/PreviewwithpreviewPath=/App_Data/license.xml - User agent:
curl/7.81.0 - All requests returned 301 redirects
- 13:03:52 UTC - Four consecutive GET requests to
-
January 28, 2024: Expanded reconnaissance on PROD CD2
- 08:40:03 UTC - Initial probe to root path
/ - 08:40:04 UTC - Asset enumeration:
/default.jsand/default.css - 08:40:04 UTC - DeviceSimulator exploit attempt with
previewPath=/App_Data/license.xml - User agents varied between
curl/7.81.0andpython-urllib3/2.1.0 - All requests returned 301 redirects
- 08:40:03 UTC - Initial probe to root path
Attack Characteristics:
- Primary Targets:
- XAML Tutorials vulnerability (SC2022-003-510463) - December 31, 2023
- DeviceSimulator vulnerability (SC2023-001-568150 / SC2023-003-587441) - January 2024
- Objectives:
- Attempted to exploit XAML Tutorials deserialization vulnerability
- Attempted to access
/App_Data/license.xmlvia the DeviceSimulator preview path bypass
- User Agents: Alternated between
curl/7.81.0,python-requests/2.25.1,python-urllib3/2.1.0, and various Chrome user agents to appear as different tools - Timing: Requests spaced seconds apart, suggesting manual testing or throttled automation
- Servers Targeted: STAGE CM (December 2023), PROD CD2 (January 2024)
- Success Rate: 0% - All attempts resulted in redirects (301/302), indicating vulnerabilities were patched or not present
Interpretation:
The attacker demonstrated knowledge of multiple Sitecore vulnerabilities and followed a methodical progression from initial reconnaissance to targeted exploitation attempts. The activity began with basic asset enumeration on STAGE CM in mid-December, escalated to a XAML Tutorials exploitation attempt on December 31, then shifted focus to the production environment (PROD CD2) in January with DeviceSimulator attacks. The variation in user agents and the progression from basic reconnaissance (checking root, JS files) to targeted exploitation attempts indicates a sophisticated, planned approach. The consistent redirect responses suggest proper security controls and patching were in place across both environments.
94.140.11.43
This IP address engaged in focused DeviceSimulator vulnerability exploitation attempts during a concentrated time window in May 2023. The activity demonstrates systematic path variation testing, attempting multiple encoding and path manipulation techniques to bypass security controls.
Activity Timeline:
-
May 18, 2023 - PROD CM
- 04:04:25 UTC - Initial DeviceSimulator exploit attempt via HTTP (port 80)
- Target:
/api/sitecore/Sitecore.Mvc.DeviceSimulator.Controllers.SimulatorController,Sitecore.Mvc.DeviceSimulator.dll/Preview - Path variations tested:
/App_Data/license.xml,\/App_Data/license.xml(escaped forward slash) - Response: 301 redirect
- Target:
- 04:04:29 UTC - Continued path manipulation testing
- Path variations tested:
/Data/license.xml,\/Data/license.xml(removedApp_prefix) - Response: 301 redirect
- Path variations tested:
- User agent:
Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/112.0.5615.138+Safari/537.36
- 04:04:25 UTC - Initial DeviceSimulator exploit attempt via HTTP (port 80)
-
May 18, 2023 - STAGING CM
- 08:33:21 UTC - DeviceSimulator exploit attempts via HTTP (port 80)
- Path variations tested:
\/App_Data/license.xml,/Data/license.xml - Response: 404 Not Found
- Path variations tested:
- 08:34:17 UTC - Additional path variation attempts
- Path variations tested:
/Data/license.xml,\/Data/license.xml - Response: 404 Not Found
- Path variations tested:
- User agent:
Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/112.0.5615.138+Safari/537.36
- 08:33:21 UTC - DeviceSimulator exploit attempts via HTTP (port 80)
-
May 18, 2023 - PROD CM
- 12:11:14 UTC - DeviceSimulator exploit attempt via HTTPS (port 443)
- Target:
/api/sitecore/Sitecore.Mvc.DeviceSimulator.Controllers.SimulatorController,Sitecore.Mvc.DeviceSimulator.dll/Preview - Path:
/App_Data/license.xml - Response: 302 redirect
- User agent:
Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/112.0.5615.138+Safari/537.36
- Target:
- 12:11:14 UTC - DeviceSimulator exploit attempt via HTTPS (port 443)
Attack Characteristics:
- Primary Target: DeviceSimulator vulnerability (SC2023-001-568150 / SC2023-003-587441)
- Objective: Attempted to access
/App_Data/license.xmlvia the DeviceSimulator preview path bypass - Tactics: Systematic path manipulation testing using multiple encoding variations:
- Standard path:
/App_Data/license.xml - Escaped forward slash:
\/App_Data/license.xml - Path traversal variation:
/Data/license.xml(removedApp_prefix) - Escaped path traversal:
\/Data/license.xml
- Standard path:
- User Agent: Consistent use of modern Chrome 112 user agent (
Chrome/112.0.5615.138) - more believable than older browser versions - Protocols: Attempted both HTTP (port 80) and HTTPS (port 443)
- Servers Targeted:
- PROD CM - 5 unique request patterns
- STAGING CM - 4 unique request patterns
- Success Rate: 0% - All attempts resulted in 301 redirects (PROD) or 404 errors (STAGING), indicating the vulnerability was not successfully exploited
- Timing Pattern: Three distinct attack windows within the same day:
- 04:04 UTC - PROD CM via HTTP
- 08:33-08:34 UTC - STAGING CM via HTTP
- 12:11 UTC - PROD CM via HTTPS
IIS Log Entries
STAGING CM:
PROD CM:
Interpretation:
The attacker's methodology demonstrates an understanding of path manipulation techniques commonly used to bypass input validation. The systematic testing of multiple path variations (/App_Data/license.xml, \/App_Data/license.xml, /Data/license.xml, \/Data/license.xml) suggests the use of an automated exploit script that iteratively tries different encoding and path traversal techniques. The attacker targeted both staging and production environments within hours of each other, indicating either reconnaissance to identify which environment was more vulnerable, or systematic exploitation attempts across all discovered Sitecore instances.
The use of a modern Chrome 112 user agent is notable, as it's more believable than older browser versions commonly used in automated attacks. The rapid-fire nature of the requests (multiple attempts within seconds) combined with the path variation testing indicates automated tooling rather than manual testing.
The varying response codes (301 redirects on PROD, 404 errors on STAGING) suggest different security configurations or vulnerability states between the environments, but in both cases, the attacks were unsuccessful in accessing the target file.
94.140.11.154
This IP address, likely operated by the same threat actor or group as 94.140.11.43 (evidenced by identical user agents and attack methodology), conducted similar DeviceSimulator exploitation attempts one day earlier on May 17, 2023. The activity demonstrates the same systematic path variation testing approach with multiple encoding techniques.
Activity Timeline:
-
May 17, 2023 - PROD CM
- 15:56:50 UTC - Initial DeviceSimulator exploit attempts via HTTP (port 80)
- Target:
/api/sitecore/Sitecore.Mvc.DeviceSimulator.Controllers.SimulatorController,Sitecore.Mvc.DeviceSimulator.dll/Preview - Path variations tested:
/App_Data/license.xml,\/App_Data/license.xml(escaped forward slash) - Response: 301 redirect
- Target:
- 15:56:51 UTC - Path traversal variations
- Path variations tested:
/Data/license.xml,\/Data/license.xml(removedApp_prefix) - Response: 301 redirect
- Path variations tested:
- User agent:
Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/112.0.5615.138+Safari/537.36
- 15:56:50 UTC - Initial DeviceSimulator exploit attempts via HTTP (port 80)
-
May 17, 2023 - STAGING CM
- 17:27:36 UTC - DeviceSimulator exploit attempts via HTTP (port 80)
- First wave:
/App_Data/license.xml,\/App_Data/license.xml - Response: 404 Not Found
- First wave:
- 17:27:37 UTC - Path traversal testing
- Path variations:
/Data/license.xml,\/Data/license.xml - Response: 404 Not Found
- Path variations:
- 17:27:57 UTC - Repeated testing sequence (same pattern as 17:27:36)
- Path variations:
/App_Data/license.xml,\/App_Data/license.xml - Response: 404 Not Found
- Path variations:
- 17:27:59 UTC - Repeated path traversal (same pattern as 17:27:37)
- Path variations:
/Data/license.xml,\/Data/license.xml - Response: 404 Not Found
- Path variations:
- User agent:
Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/112.0.5615.138+Safari/537.36
- 17:27:36 UTC - DeviceSimulator exploit attempts via HTTP (port 80)
-
May 17, 2023 - PROD CM
- 18:29:31 UTC - DeviceSimulator exploit attempts via HTTPS (port 443)
- Target:
/api/sitecore/Sitecore.Mvc.DeviceSimulator.Controllers.SimulatorController,Sitecore.Mvc.DeviceSimulator.dll/Preview - Path variations tested:
/App_Data/license.xml,\/App_Data/license.xml - Response: 302 redirect
- Target:
- 18:29:33 UTC - Path traversal testing via HTTPS
- Path variations:
/Data/license.xml,\/Data/license.xml - Response: 302 redirect
- Path variations:
- User agent:
Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/112.0.5615.138+Safari/537.36
- 18:29:31 UTC - DeviceSimulator exploit attempts via HTTPS (port 443)
Attack Characteristics:
- Primary Target: DeviceSimulator vulnerability (SC2023-001-568150 / SC2023-003-587441)
- Objective: Attempted to access
/App_Data/license.xmlvia the DeviceSimulator preview path bypass - Tactics: Identical to 94.140.11.43 - systematic path manipulation using encoding variations:
- Standard path:
/App_Data/license.xml - Escaped forward slash:
\/App_Data/license.xml - Path traversal variation:
/Data/license.xml - Escaped path traversal:
\/Data/license.xml
- Standard path:
- User Agent: Identical to 94.140.11.43 - Chrome 112 user agent (
Chrome/112.0.5615.138) - Protocols: Attempted both HTTP (port 80) and HTTPS (port 443)
- Servers Targeted:
- PROD CM - 8 unique request patterns across three sessions
- STAGING CM - 8 unique request patterns (with duplicate testing sequences)
- Success Rate: 0% - All attempts resulted in 301/302 redirects (PROD) or 404 errors (STAGING)
- Timing Pattern: Three distinct attack windows:
- 15:56 UTC - PROD CM via HTTP
- 17:27 UTC - STAGING CM via HTTP (with repeated testing at 17:27:57)
- 18:29 UTC - PROD CM via HTTPS
IIS Log Entries:
STAGING CM:
PROD CM:
Interpretation:
This IP address exhibits virtually identical attack patterns to 94.140.11.43, strongly suggesting they are part of the same threat actor's infrastructure or exploitation campaign. The identical user agent string (Chrome 112.0.5615.138), same path manipulation techniques, and sequential attack dates (May 17 for this IP, May 18 for 94.140.11.43) indicate a coordinated reconnaissance campaign.
Notable patterns include:
- Systematic progression: The attacker tested HTTP first, then HTTPS, methodically working through protocol options
- Repeated testing: On STAGING, the attacker repeated the exact same test sequence at 17:27:57 (20 seconds after the initial attempts), possibly to confirm initial 404 responses or test for rate limiting
- Multi-environment targeting: Both PROD and STAGING were tested within hours, showing comprehensive reconnaissance of the entire infrastructure
- Timing coordination: The attacks occurred across a ~3 hour window (15:56-18:29 UTC), suggesting either manual operation or throttled automated scanning
The 94.140.11.x subnet appears to be dedicated to Sitecore vulnerability exploitation, with both IPs using the same modern Chrome user agent and identical attack methodologies. The consistent 301/302/404 responses indicate the attacks were unsuccessful, but the systematic nature suggests the threat actors were building a target database for future exploitation attempts.
45.114.225.236
This IP address conducted limited but targeted DeviceSimulator vulnerability exploitation attempts in late November 2023. Unlike the more aggressive scanning patterns of other IPs, this attacker performed minimal reconnaissance with varied user agents, suggesting either a more cautious approach or testing of specific exploit variations.
Activity Timeline:
-
November 27, 2023 - STAGING CM
- 11:38:08 UTC - Initial DeviceSimulator exploit attempt via HTTPS (port 443)
- Target:
/api/sitecore/Sitecore.Mvc.DeviceSimulator.Controllers.SimulatorController,Sitecore.Mvc.DeviceSimulator.dll/Preview - Path:
/App_Data/license.xml - Response: 404 Not Found
- User agent:
Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/58.0.3029.81+Safari/537.36
- Target:
- 11:38:29 UTC - Follow-up attempt with different user agent (21 seconds later)
- Path:
/App_Data/license.xml - Response: 404 Not Found
- User agent:
Mozilla/5.0+(Windows+NT+6.1;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/58.0.3029.110+Safari/537.36+Edge/16.16299
- Path:
- 11:38:08 UTC - Initial DeviceSimulator exploit attempt via HTTPS (port 443)
-
November 27, 2023 - PROD CM
- 12:31:55 UTC - DeviceSimulator exploit attempt via HTTPS (port 443)
- Target:
/api/sitecore/Sitecore.Mvc.DeviceSimulator.Controllers.SimulatorController,Sitecore.Mvc.DeviceSimulator.dll/Preview - Path:
/App_Data/license.xml - Response: 401 Unauthorized
- User agent:
Mozilla/5.0+(Windows+NT+6.1;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/58.0.3029.110+Safari/537.36+Edge/16.16299
- Target:
- 12:31:55 UTC - DeviceSimulator exploit attempt via HTTPS (port 443)
Attack Characteristics:
- Primary Target: DeviceSimulator vulnerability (SC2023-001-568150 / SC2023-003-587441)
- Objective: Attempted to access
/App_Data/license.xmlvia the DeviceSimulator preview path bypass - Tactics: Minimal, focused testing:
- Only tested standard path
/App_Data/license.xml(no encoding variations or path traversal attempts) - No HTTP attempts - exclusively used HTTPS (port 443)
- User agent variation between attempts
- Only tested standard path
- User Agents:
- Chrome 58 on Windows 7 64-bit:
Chrome/58.0.3029.81(older, more suspicious) - Chrome 58 with Edge rendering engine:
Chrome/58.0.3029.110+Safari/537.36+Edge/16.16299
- Chrome 58 on Windows 7 64-bit:
- Protocol: HTTPS only (port 443)
- Servers Targeted:
- STAGING CM - 2 requests within 21 seconds
- PROD CM - 1 request approximately 53 minutes after STAGING attempts
- Success Rate: 0% - All attempts blocked (404 on STAGING, 401 on PROD)
- Timing Pattern:
- 11:38 UTC - Two rapid STAGING attempts (21 seconds apart)
- 12:31 UTC - Single PROD attempt (~53 minutes later)
IIS Log Entries:
STAGING CM:
PROD CM:
Interpretation:
This IP address demonstrates a notably different attack pattern compared to the 94.140.11.x subnet IPs. Key distinguishing characteristics include:
-
Minimal testing: Only attempted the basic path without encoding variations or path traversal attempts, suggesting either:
- A more targeted approach (testing only the most common exploitation method)
- A less sophisticated attacker
- Reconnaissance to identify vulnerable targets before deploying more aggressive techniques
-
User agent switching: The attacker changed user agents between the first and second STAGING attempts, possibly testing whether user agent filtering was in place or attempting to appear as different visitors.
-
Temporal spacing: The ~53-minute gap between STAGING and PROD attempts is unusual. Most automated scanners would test both environments in rapid succession. This delay suggests either:
- Manual testing rather than automated scanning
- Rate limiting in the attacker's toolset
- Analysis of STAGING results before proceeding to PROD
-
Chrome 58 user agent: The use of Chrome 58 (released in 2017) is relatively dated compared to the Chrome 112 user agents used by the 94.140.11.x subnet. This older version might be:
- An attempt to blend in with legacy systems
- Evidence of an older exploit toolkit
- Deliberately outdated to avoid modern security detection rules
-
Authentication challenges: The 401 response on PROD (vs 404 on STAGING) indicates PROD had authentication requirements that STAGING lacked, showing proper defense-in-depth security configurations.
The restrained nature of this attack - only three requests total, no encoding variations, no HTTP attempts - could indicate a "low and slow" reconnaissance strategy designed to avoid triggering automated security alerts. Alternatively, this could be an opportunistic scan from a less sophisticated attacker testing publicly documented exploitation techniques.
20.222.39.209
This IP address conducted multiple sitecore_xaml.ashx exploitation attempts in October 2023, demonstrating a methodical approach to testing the XAML deserialization vulnerability across both HTTP and HTTPS protocols.
Activity Timeline:
- October 11, 2023 - STAGING CM (Multiple Sessions)
- 12:47:42 UTC - Initial wave of sitecore_xaml exploitation attempts
- POST to
/sitecore_xaml.ashx/-/xaml/Sitecore.Xaml.Tutorials.Styles.Indexvia HTTP (port 80) - Response: 301 redirect
- POST to same path via HTTPS (port 443)
- Response: 302 redirect
- GET request to same path via HTTPS
- Response: 302 redirect
- User agent:
python-requests/2.31.0
- POST to
- 13:47:53 UTC - Second wave (~1 hour later)
- POST via HTTP → 301 redirect
- POST via HTTPS → 302 redirect
- GET via HTTPS → 302 redirect
- User agent:
python-requests/2.31.0
- 15:10:58 UTC - Third wave (~1.5 hours after second wave)
- POST via HTTP → 301 redirect
- POST via HTTPS → 302 redirect
- GET to
/sitecore/service/notfound.aspxwith parameters → 404 - GET to
/sitecore_xaml.ashx/-/xaml/Sitecore.Xaml.Tutorials.Styles.Index→ 302 redirect - GET to
/sitecore/service/notfound.aspxagain → 404 - User agent:
python-requests/2.31.0
- 12:47:42 UTC - Initial wave of sitecore_xaml exploitation attempts
Attack Characteristics:
- Primary Target: XAML deserialization vulnerability (
sitecore_xaml.ashx) - Objective: Attempted to exploit the Sitecore XAML handler for remote code execution
- Tactics:
- Systematic testing of both POST and GET methods
- Protocol testing (HTTP port 80 and HTTPS port 443)
- Multiple attempts spaced approximately 1 hour apart
- Testing of error handling pages (
/sitecore/service/notfound.aspx)
- User Agent: Consistent
python-requests/2.31.0(Python automation library) - Protocols: Both HTTP (port 80) and HTTPS (port 443)
- Server Targeted: STAGING CM exclusively
- Success Rate: 0% - All attempts resulted in 301/302 redirects or 404 errors
- Timing Pattern: Three attack windows throughout the day:
- 12:47 UTC - Initial testing
- 13:47 UTC - Retry after 1 hour
- 15:10 UTC - Final attempt after ~2.5 hours from start
IIS Log Entries:
STAGING CM:
Interpretation:
This IP demonstrates characteristics of automated scanning with deliberate timing delays between attempts. Key observations:
- Automated Python scripting: The consistent use of
python-requests/2.31.0indicates a custom Python script rather than an off-the-shelf exploit tool - Methodical protocol testing: Each attack wave tested both HTTP and HTTPS, suggesting the script was designed to identify which protocol was vulnerable
- Error page probing: The requests to
/sitecore/service/notfound.aspxin the final wave indicate the attacker was analyzing error responses to gather information about the application structure - Timing delays: The ~1 hour gaps between attack waves suggest either:
- Rate limiting to avoid detection
- Manual triggering of automated scripts
- Batch processing with scheduled intervals
- Persistent targeting: Three separate attempts over 2.5 hours shows determination despite consistent failure responses
The IP address 20.222.39.209 is registered to Microsoft Azure, indicating the attacker was using cloud infrastructure (likely compromised or ephemeral instances) to conduct their reconnaissance. The XAML vulnerability targeted is older than the DeviceSimulator vulnerability, suggesting this attacker was working through a checklist of known Sitecore exploits.
13.212.202.12
This IP address, registered to Amazon AWS in Singapore, conducted DeviceSimulator exploitation attempts across multiple dates in January 2024, targeting both STAGING and PROD environments with user agent variations.
Activity Timeline:
-
January 4, 2024 - PROD CM
- 17:54:42 UTC - Initial DeviceSimulator exploit attempt via HTTPS (port 443)
- Path:
/App_Data/license.xml - Response: 401 Unauthorized
- User agent:
Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/58.0.3029.110+Safari/537.3
- Path:
- 17:54:42 UTC - Initial DeviceSimulator exploit attempt via HTTPS (port 443)
-
January 4, 2024 - STAGING CM
- 22:08:26 UTC - First STAGING attempt via HTTPS (~4 hours after PROD)
- Path:
/App_Data/license.xml - Response: 404 Not Found
- User agent:
Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/58.0.3029.81+Safari/537.36(Windows 7)
- Path:
- 22:09:38 UTC - Follow-up attempt (72 seconds later)
- Path:
/App_Data/license.xml - Response: 404 Not Found
- User agent:
Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/58.0.3029.110+Safari/537.3(Windows 10)
- Path:
- 22:08:26 UTC - First STAGING attempt via HTTPS (~4 hours after PROD)
-
January 5, 2024 - PROD CM
- 02:47:35 UTC - Final attempt via HTTPS (~9 hours after STAGING)
- Path:
/App_Data/license.xml - Response: 401 Unauthorized
- User agent:
Mozilla/5.0+(Macintosh;+Intel+Mac+OS+X+10_12_6)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/58.0.3029.110+Safari/537.36(Mac OS X)
- Path:
- 02:47:35 UTC - Final attempt via HTTPS (~9 hours after STAGING)
Attack Characteristics:
- Primary Target: DeviceSimulator vulnerability
- Objective: Attempted to access
/App_Data/license.xml - Tactics:
- Minimal path testing (only standard
/App_Data/license.xml) - User agent rotation to simulate different OS platforms
- Testing across multiple dates
- Minimal path testing (only standard
- User Agents:
- Chrome 58 on Windows 7, Windows 10, and Mac OS X
- Protocol: HTTPS only (port 443)
- Servers Targeted: Both PROD and STAGING CM
- Success Rate: 0% - All attempts blocked (404 on STAGING, 401 on PROD)
- Timing Pattern:
- 17:54 UTC (Jan 4) - PROD
- 22:08-22:09 UTC (Jan 4) - STAGING (~4 hours later)
- 02:47 UTC (Jan 5) - PROD (~9 hours after STAGING)
IIS Log Entries:
STAGING CM:
PROD CM:
Interpretation:
This IP exhibits a sophisticated multi-day reconnaissance approach. The use of Amazon AWS Singapore infrastructure, user agent rotation across three OS platforms, and the unusual PROD-first targeting pattern suggests either manual testing or a more deliberate reconnaissance campaign. The time gaps between attempts indicate careful, methodical probing rather than rapid automated scanning.
175.178.248.154
This IP conducted some of the earliest DeviceSimulator exploitation attempts observed, appearing just 5 days after the public disclosure in May 2023, with extensive user agent rotation spanning multiple operating systems.
Activity Timeline:
-
May 15, 2023 - PROD CM (Six Attempts)
- 08:11:54 UTC - Initial attempt
- User agent: Windows XP, Chrome 35
- Response: 302 redirect
- 08:22:07 UTC - Second attempt
- User agent: Windows 10 Technical Preview, Chrome 41
- Response: 302 redirect
- 09:13:27 UTC - Third attempt
- Same user agent as 08:22:07
- Response: 302 redirect
- 09:15:52 UTC - Fourth attempt
- User agent: Ubuntu Linux, Chrome 53
- Response: 302 redirect
- 09:17:55 UTC - Fifth attempt
- User agent: Windows XP, Chrome 36
- Response: 302 redirect
- 09:26:25 UTC - Sixth attempt
- User agent: Mac OS X Yosemite, Chrome 41
- Response: 302 redirect
- 08:11:54 UTC - Initial attempt
-
May 15, 2023 - STAGING CM (Four Attempts)
- 08:30:22 UTC - Initial attempts (two simultaneous user agents)
- Mac OS X, Chrome 49
- Windows 10, Chrome 89
- Response: 404 Not Found
- 09:33:39 UTC - Follow-up
- User agent: Windows XP, Chrome 41
- Response: 404 Not Found
- 09:33:42 UTC - Final attempt
- User agent: Windows 8.1, Chrome 41
- Response: 404 Not Found
- 08:30:22 UTC - Initial attempts (two simultaneous user agents)
Attack Characteristics:
- Early adopter: Just 5 days after public disclosure
- Extensive user agent rotation: 8+ different user agents across Windows XP, 7, 8.1, 10, Mac OS X, and Ubuntu Linux
- Legacy OS simulation: Multiple Windows XP user agents (end-of-life OS)
- Methodical timing: Variable intervals (2-51 minutes)
- Cross-platform approach: Comprehensive testing across all major OS platforms
- Success Rate: 0% - All blocked
IIS Log Entries:
PROD CM (excerpt):
Interpretation:
The combination of early timing (5 days post-disclosure), extensive user agent diversity, and methodical testing patterns suggests either a security researcher conducting analysis or an advanced threat actor rapidly incorporating new exploits. The use of legacy OS user agents (Windows XP) alongside modern systems and the cross-platform approach indicates comprehensive testing methodology.
40.85.160.229
This Microsoft Azure IP conducted DeviceSimulator exploitation in February 2024 using an advanced technique: HTTP Parameter Pollution (HPP) through parameter doubling, representing a more sophisticated attack vector than standard testing.
Activity Timeline:
- February 3, 2024 - PROD CM
- 22:31:19 UTC - Initial attempt via HTTP (port 80)
- Standard path:
previewPath=/App_Data/license.xml - Response: 301 redirect
- User agent: Firefox 121 (very recent at the time)
- Standard path:
- 22:31:19 UTC - Parameter pollution via HTTPS (same second)
- Unique attack:
previewPath=/App_Data/license.xml&previewPath=/App_Data/license.xml - Doubled the parameter name in the query string
- Response: 401 Unauthorized
- Unique attack:
- 22:31:29 UTC - Retry (10 seconds later)
- Same doubled parameter attack
- Response: 401 Unauthorized
- 22:31:19 UTC - Initial attempt via HTTP (port 80)
Attack Characteristics:
- Unique Tactic: HTTP Parameter Pollution (HPP)
- Tests inconsistent parameter handling across system layers
- Web servers vs application frameworks may process parameters differently
- Can bypass security filters that only validate first occurrence
- Modern tooling: Firefox 121 (very recent)
- Azure infrastructure: Microsoft cloud
- Rapid testing: 10-second retry
- Single environment focus: PROD only
- Success Rate: 0% - All blocked
IIS Log Entries:
PROD CM:
Interpretation:
This IP demonstrates notably advanced techniques. The HTTP Parameter Pollution attack tests whether different system components handle duplicate parameters differently - a sophisticated bypass technique. Combined with modern Firefox 121 user agent and Azure infrastructure, this suggests either an advanced exploitation framework or a skilled security researcher. The focused, rapid testing approach differs markedly from the broad scanning patterns of other IPs.
What to Look For
Check for requests to these paths in your logs to help identify threat actors. In addition to my suggestions, I recommend reading the articles linked at the end of this post to help identify more keywords to search for.
/api/sitecore/Sitecore.Mvc.DeviceSimulator.Controllers.SimulatorController/sitecore/shell/ClientBin/Reporting/Report.ashx/sitecore/shell/Invoke.aspx/sitecore/shell/~/xaml/Sitecore.Xaml.Tutorials.Styles.Index/api/sitecore/Sitecore.Mvc.DeviceSimulatorExecute.aspx?cmd=Service2.asmxSitecore.Rocks.Validation.ashxWeb.configBrowse.aspx- Any paths starting with
/bin /Telerik.Web.UI.WebResource.axd/sitecore/shell/api/sitecore/ExperienceExplorerSelectUser.xaml/sitecore modules/PowerShell/sitecore/shell/Applications/WebEdit/sitecore modules/Web//api/sitecore/cmd.exe- Any paths containing
../or%2e%2e%2f(URL encoded../) /sitecore/login/sitecore/admin<script>javascript:/sitecore/client/Applications?cmd=?exec=.config/sitecore/service/sitecore/api/ssc/item/App_Data/diagnostics
Also check your Sitecore logs for:
Scripts and Tools for Log Analysis
Log Parser Studio
I found Log Parser Studio to be helpful in analyzing IIS logs.
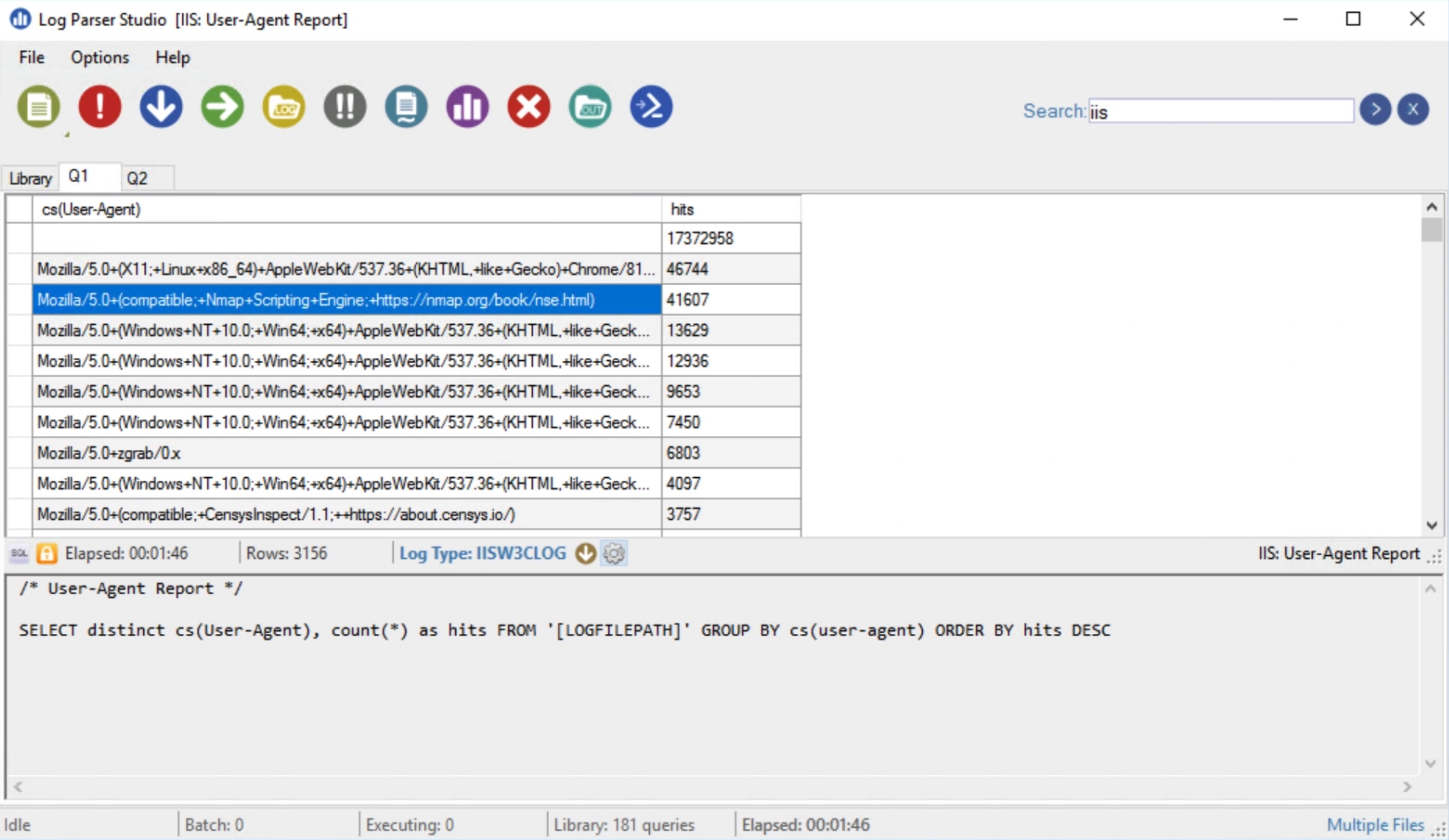
The queryable fields are:
Some useful queries follow.
PowerShell Scripts for Scanning IIS Logs
Reflection and Action Items
Question Checklist
For every security bulletin, you should be able to answer "yes" to all of the following questions:
- Do you know when the vulnerability was announced?
- Do you know when the patches were applied?
- Do you know which roles the patches needed to be applied to? Were they?
- Were patches applied to all environments / servers / roles (CM, CD, xConnect, etc.)?
- Were patches applied before the first exploit attempts?
- Do you have a process in place to monitor for these types of attacks?
- Do you have a process in place to block IPs that are attempting to exploit these vulnerabilities?
Miscellaneous Action Items
- Block user agents containing
zgrabbecause the tool is used to collect info on TLS handshakes. - Block all incoming requests to your servers except those originating from a trusted WAF provider.
- Have tools and automations in place to scan your IIS, Sitecore, and system logs.
- Employ a push notification system rather than engaging in manual log reviews in which reconnaissance and exploits can easily be missed.
- Ensure that your TLS / encryption ciphers are configured properly. This is a common attack vector for hackers. You can use a tool like https://www.ssllabs.com/ssltest/ or https://www.immuniweb.com/ssl to check your server's configuration.
- Turn off your default IIS sites.
- Explore tools such as https://www.nartac.com/Products/IISCrypto to disable insecure ciphers and protocols.
- Use country blocking when possible for maximum protection with the least amount of effort.
- Use a WAF.
- Keep your Sitecore installation up to date with the latest security patches.
- Monitor your logs for suspicious activity.
- Whenever you see a critical vulnerability bulletin, perform an extensive log search for keywords which appeared in the bulletin and in the contents of the hotfix files themselves. This will help you identify if the vulnerability was exploited in your environment.
- Run a full scan on your server to ensure that no malware has been installed.
- Check inetpub/history to check for config history changes.
- Subscribe to the Sitecore Security Bulletin to stay up to date with the latest security vulnerabilities: https://support.sitecore.com/kb?id=kb_search&kb_knowledge_base=44035465db70dc109e54320a689619bf.
IIS URL Rewrites
Below is a sample set of IIS rewrite rules to get you started on blocking known malicious IPs, paths, and query strings.
Bug Bounties
Sitecore has a bug bounty program: https://www.sitecore.com/legal/security:
If you discover a security bug or vulnerability on a Sitecore website, please report it by sending an email to
securityvulnerability@sitecore.com. Sitecore partners with HackerOne, and depending on the scope and criticality of the issue, it may be eligible for a reward.
Help Others
Report cases of abuse. In this case, I reported the offending IP address to the hosting providers. This may deter the hackers from exploiting other sites.
Additional Reading
- Raw Logs: xm-vulerability-exploit-attempts-raw-logs.txt
- Blocking Malicious Bots with IIS
- https://www.assetnote.io/resources/research/sitecore-experience-platform-pre-auth-rce-cve-2021-42237
- https://caesarevan23.medium.com/how-i-get-pre-auth-remote-code-execution-cve-2021-42237-on-one-of-the-vendors-f62e35cb90de
- https://github.com/ItsIgnacioPortal/CVE-2021-42237
- https://medium.com/nerd-for-tech/a-defenders-perspective-of-sitecore-xp-deserialization-rce-cve-2021-42237-dcd5355ca591
- https://vulners.com/nuclei/NUCLEI:CVE-2021-42237
- https://code-white.com/blog/exploiting-asp.net-templateparser-part-1/
Disclaimer
This analysis is not exhaustive. Same applies to the recommendations. There are almost certainly some paths that were missed. Go through the blog posts outlining the vulnerabilities and verify for yourself!
Stay vigilant,
-MG





